There are several recent instances of protection breaches where the access point was one of these unsafe, low-level IoT processors attached to a larger network. As a result, securing these devices by executing future-proof security devices that are fast, tiny, and also of training course safe, is imperative for executing a safety method that encompasses all connected tools. We lately partnered with ON Semiconductor to attend to the safety and security requirements of the RSL10, a versatile multi-protocol System on Chip (SoC) that brings ultra-low-power Bluetooth Low Power to several applications.
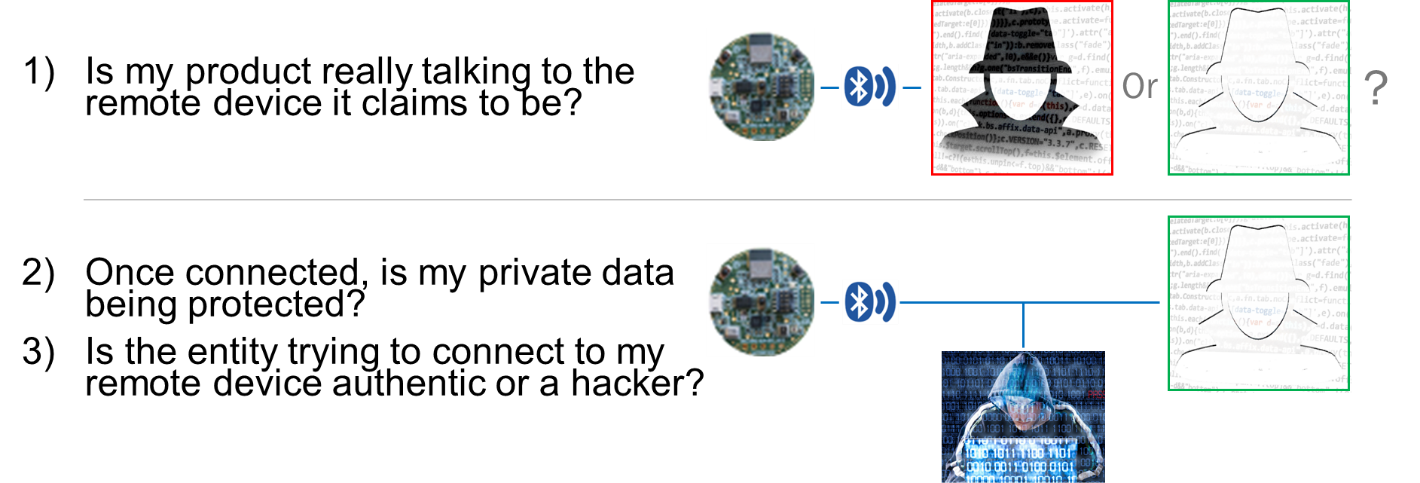
Figure 1. IoT Safety Concerns
The ON Semiconductor RSL10 radio family members that brings ultra-low-power Bluetooth 5 ability to cordless applications. The SoC is ideal for numerous IoT applications and also numerous users will likely require additional attributes such as device-to-device safety and/or information protection. Carrying out these protection attributes can make certain an RSL10 device is truly talking with the licensed remote gadget it is expecting. Or once the device is linked, includes that make certain the personal information is secured during transmission as well as the request for data is coming from an authenticated entity. Veridify Safety and security’s public key approaches authentication and data defense, as well as support for DOME ™, Veridify’s zero-touch onboarding, blockchain ownership monitoring, and registration option.
Veridify’s safety and security remedies can be applied in software-only (for instance, running on the RSL10’s Arm ® Cortex ®- M3 processor) and also require little memory, making them easy to use as well as fit for IoT applications in the industrial, medical, automobile, and also consumer areas.
As an ON Semiconductor Cybersecurity Ecosystem companion, Veridify Protection supplies turnkey security solutions, which helps to accelerate protected RSL10 item advancement.
RSL10 Safety Option
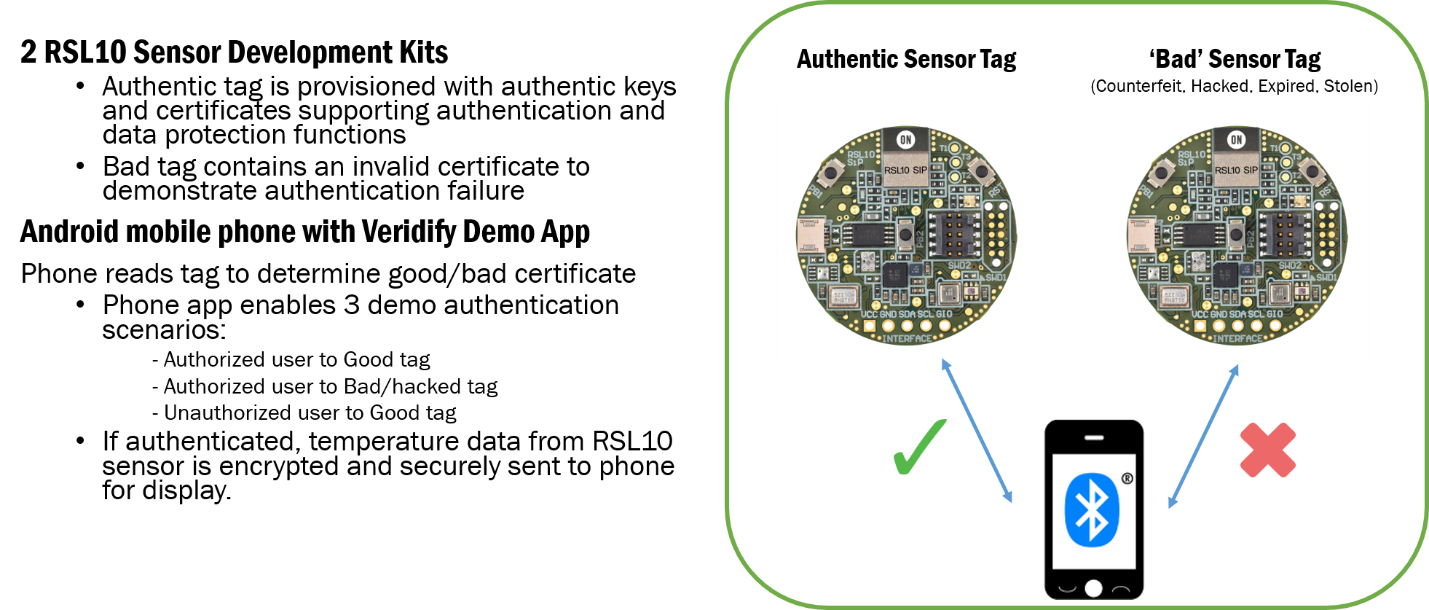
Figure 2. RSL10 Safety Remedy with Veridify
The firms have produced a presentation showing how Veridify Safety and security’s methods can be leveraged to conveniently execute device-to-device protection on the RSL10 Bluetooth Low Power SoC. The demo utilizes an RSL10 sensor board set with Veridify’s safety methods, equally authenticating with a smart device over Bluetooth Low Energy. Real-time temperature information collected by the RSL10 will be encrypted and also sent to the phone for screen if both endpoints (phone as well as sensor) are genuine. An imitation tag as well as unauthorized individual are additionally given to demonstrate how the system can determine unapproved customers and bad sensing units. The demo shows that by utilizing Veridify Security’s software, it is easy to secure IoT edge tools based on RSL10
Veridify Security tools now available via CMSIS-pack for RSL10.
Veridify Safety devices are ISO 26262 ASIL D certified and are now offered for the RSL10 in the form of a CMSIS pack offering programmers with a familiar interface for easy implementation. Executing powerful security applications like device-to-device authentication, data security, and the safe and secure firmware upgrade is now less complicated than ever before.


